Is Cyberterrorism an Exaggeration?
Homeland Security Director Tom Ridge said :
“Terrorist can sit at one computer connected to one network and can create worldwide havoc. They don’t necessarily need a bomb or explosives to cripple a sector of the economy or shut down a power grid”.
Even before September 11, former President Bush was fervently depicting an America imminently in danger of an attack by cyberterrorist, warning during his presidential campaign that "American forces are overused and underfunded precisely when they are confronted by a host of new threats and challenges--the spread of weapons of mass destruction, the rise of cyberterrorism, and the proliferation of missile technology."
However, according to Joshua Green in an article “The Problem of Cyberterrorism Is Exaggerated”, there is no such thing as cyberterrorism. There is no instance of anyone ever having been killed by terrorist (or anyone else) using a computer. Nor is there compelling evidence that al-Qaeda or any other terrorist organization has resorted to computers for any sort of serious destructive activity. He even wrote:“What more outside of a Tom Clancy novel, computer security specialists, believe it is virtually impossible to use the Internet to inflict death on a large scale, and many scoff at the notion that terrorist would bother trying.”
According to Dorothy Denning, a computer science professor at Georgetown University and one of America’s foremost cybersecurity experts, “Not only does [cyberterrorism] not rank alongside chemical, biological, or nuclear weapons, but it is not anywhere near as serious as other potential physical threats like car bomb, or suicide bombers.”
This does not mean that cybersecurity is not a serious problem. It just means that in the context of cyber space and terrorist, it is not the problem that the public thinks it is.
Terrorist and computer security experts, and current and former government and military officials, almost unanimously agree that the real danger is still from the criminal and other hackers who did $15 billion in damage to the global economy last year using viruses, worms and other readily available tools.
In Joshua Green’s article he also commented that the current public imagine of cyberterrorism is as those along Hollywood plots lines in which terrorist hijack nuclear weapons, airlines or military computers from halfway around the world. First, the idea that nuclear weapons can be remotely controlled is the biggest fallacy promoted by action thrillers. Martin Libicki, a defense analyst at the RAND Corporation states that “Movies are premised on the assumption that there is a modem bank hanging on the side of the computer that controls the missiles; I assure that there is none. Rather nuclear weapons and other sensitive military systems enjoy the most basic form of Internet security; they are “air-gapped” meaning that they are not physically connected to the Internet and are therefore inaccessible to outside hackers.”
Referring to the September 11 catastrophe, the September 11 hijackings led to an outcry that airliners are particularly susceptible to cyberterrorism. Sen. Charles Schumer (D-N.Y.) described "the absolute havoc and devastation that would result if cyberterrorists suddenly shut down our air traffic control system, with thousands of planes in mid-flight."
In fact, cybersecurity experts give some of their highest marks to the FAA, which reasonably separates its administrative and air traffic control systems and strictly air-gaps the latter. And there's a reason the 9/11 hijackers used box-cutters instead of keyboards: It's impossible to hijack a plane remotely, which eliminates the possibility of a high-tech 9/11 scenario in which planes are used as weapons.
What about the less-protected secondary targets that is the power grids, oil pipelines, dams and water systems?
These systems are mostly in the private sector or in Malaysia’s context are Government Link Corporations. Thus, it is true that they tend to be less secure than government and military systems. In addition, many of these companies do use the Internet to manage certain processes.
However, in June, the Washington Posts illustrates the supposed ease with which a cyberterrorist could subvert a dam by publishing a story on al-Qaeda cyberterrorism. The article related an anecdote about a 12-year old who hacked into the SCADA system at Arizona’s Theodore Roosevelt Dam in 1998 and the article intimated that the boy was within mere keystrokes of unleashing millions of gallons of water upon helpless downstream communities. The reality is that subsequent investigation by tech new site CNet.con revealed the tale is apocryphal. The incident actually occurred in 1994, the hacker was 27 years old and the investigators concluded that although he did hack but he could not have gained any control of the dam.
Most hackers break in as sport. Of course it is possible that a computer literate terrorist intent on wreaking havoc could hack into a computer at a dam but what happens once the system is accessed. The hacker may have gained access but maneuvering within the system such that the hacker can cause any damage is more difficult than the public understand. Few besides a company’s own employees actually possess the specific technical expertise required to manipulate the system. There was an incident in Australia where a man used an Internet connection to release a million gallons of sewage along the Queensland’s Sunshine Coast after being turned down a government job. When police arrested him, they discovered that he worked for the company that designed the sewage treatment plant’s control software. So, terrorist may recruit such insiders but again, causing damage is more difficult than the public understands because the corporations do have contingency plans.
Take for example, when the U.S. Naval War College contracted with a research group to simulate a massive attack on the nation's information infrastructure. Government hackers and security analysts gathered in Newport, R.I., for a war game dubbed "Digital Pearl Harbor." The result? The hackers failed to crash the Internet, though they did cause serious sporadic damage. But, according to a CNet.com report, officials concluded that terrorists hoping to stage such an attack "would require a syndicate with significant resources, including $200 million, country-level intelligence and five years of preparation time."
The reality is that, despite all the media alarm of terrorist poised on the verge of cyberattack, when the US troops recovered the al-Qaeda laptops, although the officials were surprised to find its members more technologically adept than believed, nothing in their laptop suggest they were planning any cyberattacks.
What was found only proves that they were using the internet to communicate and coordinate physical attacks.
However, despite all that, there is an issue of cybersecurity and the one very real risk is economic, e-commerce. The $15 billion in damage caused by cyberattacks last year is derived mostly from worms, viruses, denial-of-service attacks, and theft, all of which capitalized on the generally lax cybersecurity in the private-sector businesses that comprise about 85 percent of the Internet.
Refer:
The Myth of Cyberterrorism; There are Many Ways Terrorist Can Kill You-Computers Aren't One of Them, by Joshua Green
----------------------------------------------------------------------------------------------------------------------------------
The Problem with Cyberterrorism by Elina Noor
The author talks and discussed on the many ambiguities of cyber terrorism in which she discussed on 4 issues
1st issue: references to the term “cyber terrorism”
The author states that cyber terrorism offers the projection of an unparalleled dimension in which the virtual and physical realms can collide in which the damages would be devastating and no cross-border laws have yet adequately transcend it.
2nd issue: why cyber terrorism would even be an option as influencing factors of decisions
3rd issue: assess the charge that cyber terrorism is an exaggerated threat
4th issue: the likely perpetrators of cyber terrorism
The Centre for the Study of Terrorism and Irregular Warfare at the Naval Postgraduate School in Monterey, California considered 5 terrorist group types: religious, New Age, ethno-nationalist separatist, revolutionary and far-right extremist.
(This paper is written by Elina Noor which appeared in SEARCCT’s Selection of Articles, Vol. 2/2011, pp.51-63)
Click here for further reading
Click here for further reading
----------------------------------------------------------------------------------------------------------------------------------
A Denial of Service Attack Through You
It is feasible for cyberterrorism to bring down the Internet through the means of
Denial of Service (DoS) attack.
The technical feasibility has already been demonstrated in a series of attacks like Code Red I, Code Red II and Nimba (recent computer virus outbreaks). Each of these attacks exploited a known software weakness in one of the millions of servers and workstations connected to the internet. These software weaknesses can be exploited to create “cascading failures’, which is a self-replicating failure that induces further failures.
A DoS attack is actually a malicious attempt by a single person or a group of people to cause the victim, site or node to deny service to customers. When this attempt is derived from a single host of the attack it constitutes only as a DoS attack. A DoS attack is aimed at denying authorised persons access to a computer of computer network.
Do not underestimate this form of attack, the results of these attacks are disastrous especially when victims are not individuals but companies. In January 2002, Cloud Nine, a UK based Internet Service Provider was forced to shut shop after a week long of DoS attack resulted in the complete stoppage of its service.
DDoS attacks have 2 characteristics. First is flooding the network with useless packets, for example, prevents legitimate ICMP echo packets from travelling over the network. Secondly, attackers try to consume CPU Power. By generating several thousands of useless processes on the victim’s system, attackers manage to fully occupy memory and process tables. Thus the victim’s computer cannot execute any process and the system breaks down. This method enables the attacked to prevent clients from assessing the victim’s services and disrupts the current connection.
DDos attacks prevent victims from either using the Internet or being reached. Consequently, when the victim is an Internet Service Provider, the results of such attacks are severe because their clients will not receive service. Being offline for a few hours could result in lost of large sums of money. DoS are a major threat to E-commerce.
Now what if the perpetrator refines his attack, and a lot of malicious hosts coordinate to flood the victim with an abundance of attack packets, so that the attack take place simultaneously from multiple points. This type of attack is called a Distributed Denial of Service( DDoS) attack.
DDoS danger was only apparent in early February 2000 when a series of attacks knocked popular sites such as Yahoo, CNN and Amazon off the air. Thus, now DDoS has been classified as a tools and methodologies of Cyberterrorism. Believe it or not, Denial of Service attack almost caused the collapse of a country in the case of Estonia.
In 2007, Estonia fell victim to a wave of computer assault on companies and institutions. The attacks disabled the websites of banks, newpapers, schools and public organization. This caused chaos in a country where over 60% of the population daily connects to Internet to check the decisions of its Cabinets, contact the doctor by videoconference, carry out all kinds of business operations and even connect to the Internet to electronically vote in the general election. The DDoS attack on Estonia lasted for several weeks and caused such an impact that Jaak Aaviksoo, the Estonian Defence Minister compared the attack to a terrorist action.
The objective of a DDoS attack is to exhaust the victim’s resources. These resources can be network bandwidth, computing power or operating system data structures.
But how does DoS and DDoS attack happen? To launch a DDOS attack, malicious users first build a network of computers that they will use to produce the volume of traffic needed to deny service to computer users. To create this attack network, attacker first discovers vulnerable sites or host on the network. The vulnerable hosts are then exploited by attackers who use their vulnerability to gain access to these hosts.
The next step for the intruder is to install new programs on the compromised host of the attack network. The hosts that are running these attack tools are known as zombies, and they can carry out any attack under the control of the attacker. Many zombies together form an army.
In a typical DDoS attack, the army of the attacker consists of master zombies and slave zombies. The hosts of both categories are compromised machines that have arisen during the scanning process and are infected by malicious code. The attacker coordinates and orders master zombies and they, in turn, coordinate and trigger slave zombies. More specifically, the attacker sends an attack command to master zombies and activates all attack processes on those machines, which are in hibernation, waiting for the appropriate command to wake up and start attacking. Then, master zombies, through those processes, send attack commands to slave zombies, ordering them to mount a DDoS attack against the victim. In that way, the agent machines (slave zombies) begin to send a large volume of packets to the victim, flooding its system with useless load and exhausting its resources.
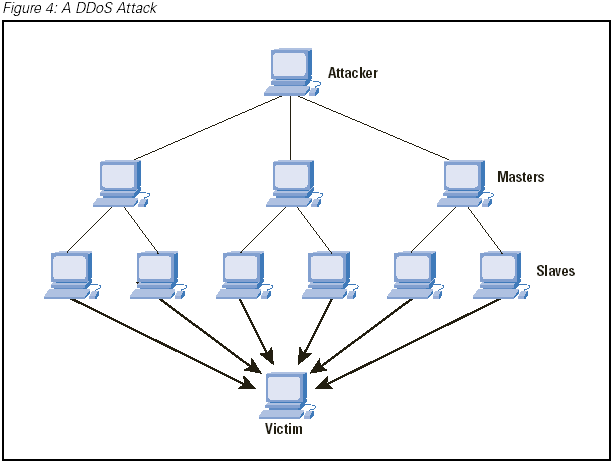 |
| Taken from the Internet Protocol Journal-Volume 7, Number 4: Distributed Denial of Service Attacks by Charalampos Patrikakis, Michalis Masikor nd Olga Zouraki from the National Technical university of Athens. |
----------------------------------------------------------------------------------------------------------------------------------
Assessing the Risks of Cyber Terrorism, Cyber War and Other Cyber Threat by James A.Lewis
James Andrew Lewis is a senior fellow and director of the Technology and Public Policy Program CSIS. Before joining CSIS, he worked at the Departments of State and Commerce as a Foreign Service officer and as a member of the Senior Executive Service. His current research examines the political effect of the Internet, strategic competition among nations, and technological innovation.
His article on assessing the risk of cyber terrorism, cyber war and other cyber threats expose to readers issue on cyber terrorism, the problem that the world is facing currently and mainly on assessment on the cyber threats. The writer trying to explain to the readers on how the advance technology that will help the growth of cyber terrorism.
According to James, there are four elements. First, we need to put cyber-warfare and cyber-terrorism in the historical context of attacks against infrastructure. Strategies that emphasize attacks on critical civil infrastructures have discussed for more than eighty years. Second, we need to examine cyber attacks against a backdrop of routine infrastructure failures. There is extensive data on power outages, flight delays and communications disruptions that occur normally and the consequences of these routine failures can be used to gage the effect cyber-warfare and cyber-terrorism. Third, we need to measure the dependence of infrastructure on computer networks and the redundancy already present in these systems. Finally, for the case of cyber-terrorism, we must consider the use of cyber-weapons in the context of the political goals and motivations of terrorists, and whether cyber-weapons are likely to achieve these goals.
In this article, the writer also explain on how terrorist attack in infrastructure and bring effect to the economy, military and so forth. The writer illustrate with infrastructure that might targeted by the terrorist in United States of America. The writer also discuss on the strategy that taken by the United States government on tackle the issues of cyber terrorism.
You can find the real incident that happened and reported in United States in this article as well. It will give you clearer picture on what cyber terrorism is all about.
For further reading, Click Here.
----------------------------------------------------------------------------------------------------------------------------------Critical Infrastructure and Cyber Terrorism by Christine Stagnetto
An article by Christine Stagnetto-Sarmiento from Oglala Lakota College, USA that mainly write about the attacks from terrorist in cyber space towards the infrastructure of one’s nation. This article provides the information of cyber attacks to the infrastructure which is quite a new idea to discuss on.
The writer first introduces the concept of terrorism and discusses it from different perspectives such as legal, policing strategies and organization changes. In this article, the author explains to the reader why cyber space becomes target of the terrorist. Terrorists can enact their acts of terror from the comfort of their own homes often half way around the world, and do not have to pass through airport security screening in person to affect their harm.
One of the main objectives of cyber terrorism is infiltration of computer systems or “hacking.” Compromised systems can then be directly manipulated or controlled by the hacker or the perpetrator can leave a “backdoor” or weakness in the computer’s security that allows the hacker to easily return and control the system later. Cyber terrorists also create attacks using viruses for damaging information. Cyber terrorists can paralyze one nation or any other country by focusing their assault on the financial system; it can debilitate any nation. The most critical infrastructures are energy, banking and finance, transportation, telecommunications, water, human services, and so forth.
The author also discusses from the social and psychological site where terrorist behavior is unpredictable, and the culture is another subject of studies. Nations need to understand the different mechanisms involved in terrorism behavior, and such understanding must be comprehensive to include the social, physiological, political, and cultural aspects. The terrorist behavior aspires to attain different goals, and external objectives.
This article mainly explains to the readers how cyber terrorism evolved in cyber space. In the conclusion the author mentions on the recommendation on prevention steps to for the government such as establish a body that handle this cyber attacks for the government and so forth.
For further reading, Click Here.
----------------------------------------------------------------------------------------------------------------------------------
No comments:
Post a Comment